When we polled business leaders earlier this year on IT concerns, we heard one reoccurring sentiment: “Am I going to walk in tomorrow and find there’s an IT problem I didn’t see coming?”
Last week, we completed our webinar series. “Explore a Cyber Attacker’s Mindset” is aimed at understanding how cyber attackers select and identify targets. This knowledge gives you an advantage in protecting your organization.
Below is a recap of the main points we shared and a link to a recording of the presentation led by Ben Fishbune, the Director of Business Development, a Solutions Architect, and a member of the leadership team at Xamin.
The Hacker's Mindset
The hacker is often portrayed in media as a shady character with a concealed face. The reality is they likely look like your average employee—just with a better understanding of technology and a strong, developed skill of social engineering that allows them to manipulate others into giving vital information.

There are different types of hackers, including:
- White hats: The “good guys” who follow the rules and work with companies to obey responsible disclosure laws.
- Grey hats: Hackers with good intentions who don’t always operate within the confines of the law and often follow their own morality to further their celebrity or a political cause.
- Black hats: The cyber criminals who look to do damage and are often part of organized crime groups.
According to the Verizon 2020 Data Breach Investigation Report, 70% of data breaches were perpetrated by external actors, and 55% of those individuals belonged to an organized crime group. The three most common ways individuals were able to get into a system were direct hacking (45%), internal errors, such as making private information public (22%), and social attacks, such as phishing or email fraud (22%).
Of the cyberattacks reported last year, 86% were financially motivated. Victims of cyberattacks are often large business, most likely due to better financial outcomes for the hackers and more users to compromise. However, 28% of breaches involved small businesses, and with hackers increasingly focused on compromising supply chains, even partnering with larger vendors can make small businesses a more enticing target. Attackers often see smaller companies as a way into larger targets because of their less developed IT services.
Cybercriminals are patient and determined. Though cyberattacks may seem to happen quickly to those who become their victims, the processes of a cybercrime can take months and involves slow probing of an organization’s vulnerabilities.
Cost to Your Organization
The costs of data breaches have risen in the past year by 10%, the largest increase in the past seven years. The global average cost of a data breach $4.24 million, and in the United States, that average is $9.05 million—a 5% increase over the last year.
According to IBM Security 2021 Cost of a Data Breach Report, the highest cost for organizations to incur during a data breach is in the form of lost business (38%). This can come in many forms such as business disruption and revenue losses from system downtime, the cost of lost customers, the cost of acquiring new customers, and the loss of reputation.
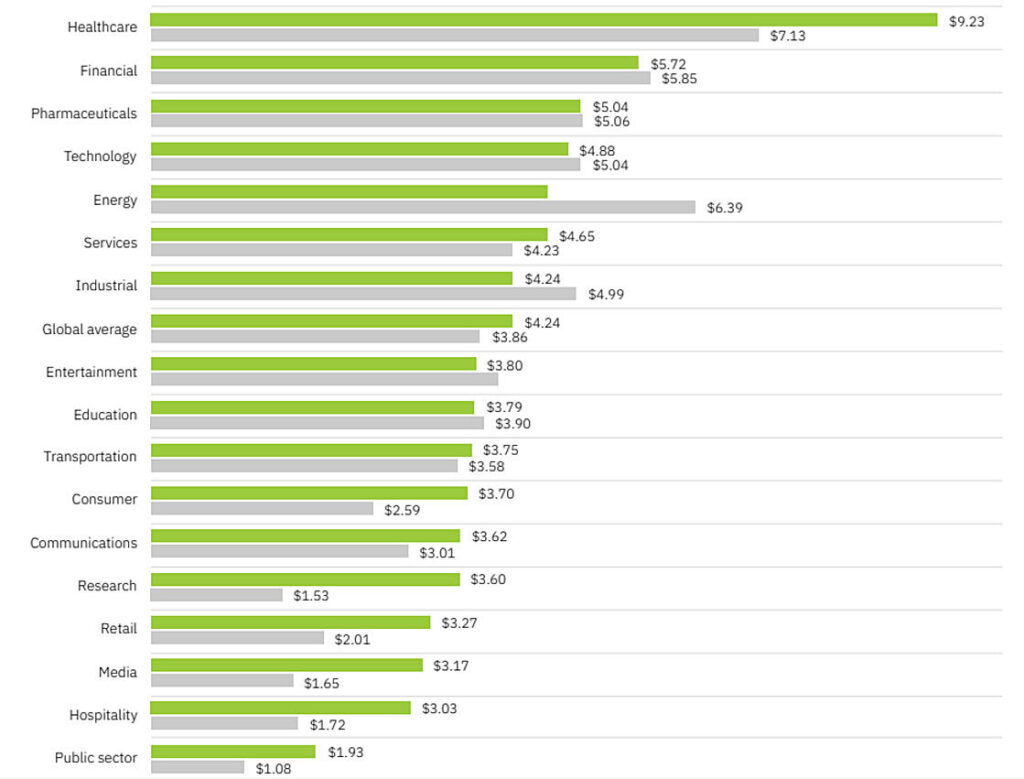
The top five industries affected were:
- Healthcare ($9.23 million)
- Financial ($5.72 million)
- Pharmaceuticals ($5.04 million)
- Technology ($4.88 million)
- Energy ($4.65 million)
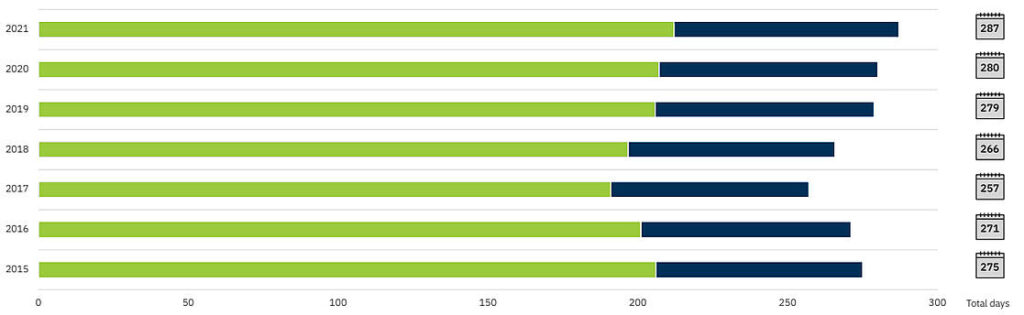
In 2021 it took an average of 212 days to identify a breach and an average 75 days to contain a breach, for a total lifecycle of 287 days. To put it into perspective, that means if a breach occurred on January 1st, it would not be contained until October 14th. Think of the damage that could be done to your company, data, and reputation in that time. The longer a data breach takes, the more costly it is to your organization.
Penetration testing
Penetration testing, or pen testing, is a wholistic approach to challenging a network’s security using the ever-evolving methods and techniques of hackers in order to then fortify that network’s security.
When pen testing to commit a crime, cybercriminals can attack in five distinct areas:
- Network Infrastructure: This is the most common type of pen test and includes intercepting network traffic, stealing credentials, exploiting networking services, etc.
- Web Application: This takes advantage of workloads moving to the cloud and remote work becoming more common.
- Wireless: Identifies and exploits insecure wireless network configurations and weak authentication. This is most successful when corporate employees use their devices on guest networks. (Thank you, local coffee shop!)
- Social Engineering: Involves the manipulation of employees through phishing, baiting, and pretexting and allows small employee mistakes to grant their attackers access into the internal network.
- Physical: The final attack occurs when someone is able to gain access into an office or to find discarded or stolen materials that can compromise security. A lost or stolen computer or smartphone can be a direct opening to a company.
Similarly, pen testing can also be done by third-party IT companies to help security. By launching a cyberattack simulation, a trusted advisor can find your organization’s potential weaknesses—and then look ways to improve upon them and prevent breaches from occurring.
Five-minute Risk Assessment
To assess the risk of a cyberattack on your organization, ask yourself:
- As a firm leader, do you feel like you are aware of the cyber risks your business faces?
- Do you understand the full impact a breach could have on your company?
- Do you have some portion of your employee base that works or accesses data remotely?
- Do you feel employees in your organization properly trained in cyber security best?
- Do you have a comprehensive incident response plan and do you test and/or review it?
We would guess the answers you gave to some or all of these questions may mean your organization is at risk.
Keeping Your Company Safe
In order to keep your organization safe, you must understand your points of vulnerability. Pen testing is a great first step in mitigating risk as it outlines where your organization has failed to fortify itself.
Next, you can transfer risk through cybersecurity insurance as a proactive risk management strategy. Usually, these policies will also require an independent IT assessment to be completed within the past year since it will show both your company’s current risk as well as your willingness to improve security.
These assessments come in two forms:
- Cybersecurity Assessment: An onsite or remote assessment that gives a clear picture of the current IT practices and their vulnerabilities. It establishes a baseline to measure all future mitigating efforts and typically takes 3-4 weeks.
- Strategic IT Review: A deep dive into all areas of the IT infrastructure and policies that provides recommendations and initiatives to mitigate risk. This process is onsite and takes 2-6 weeks to complete.


